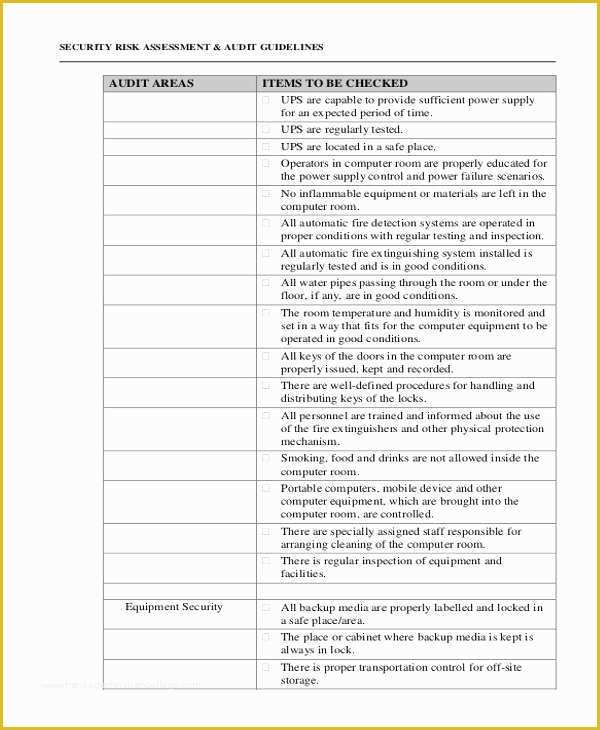
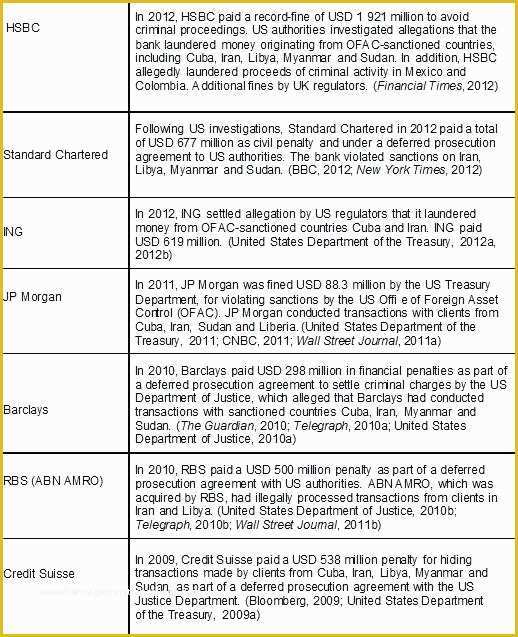
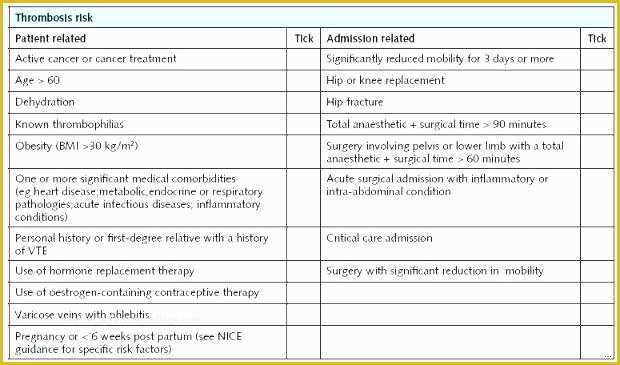
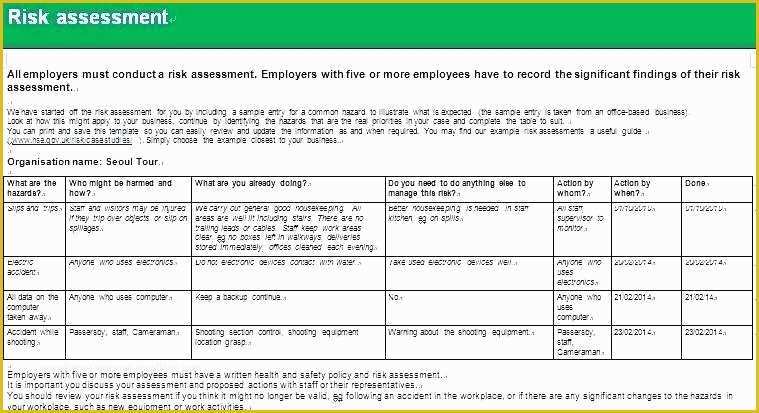
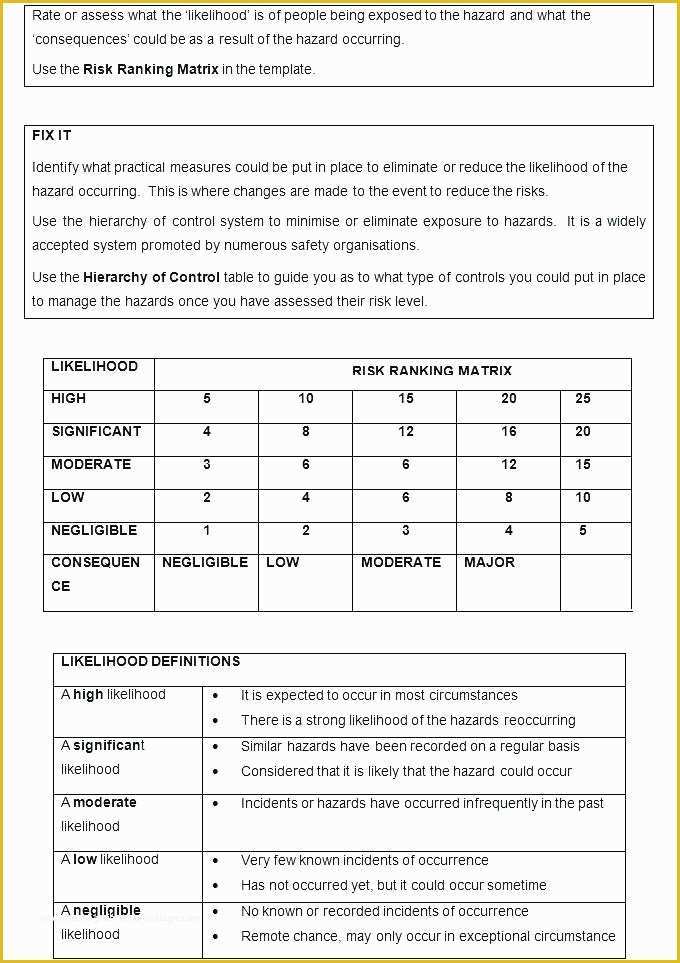
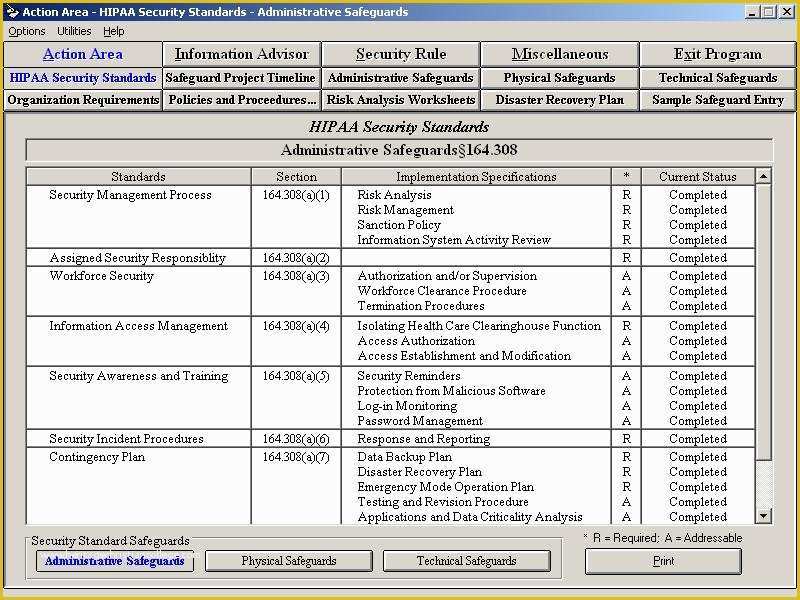
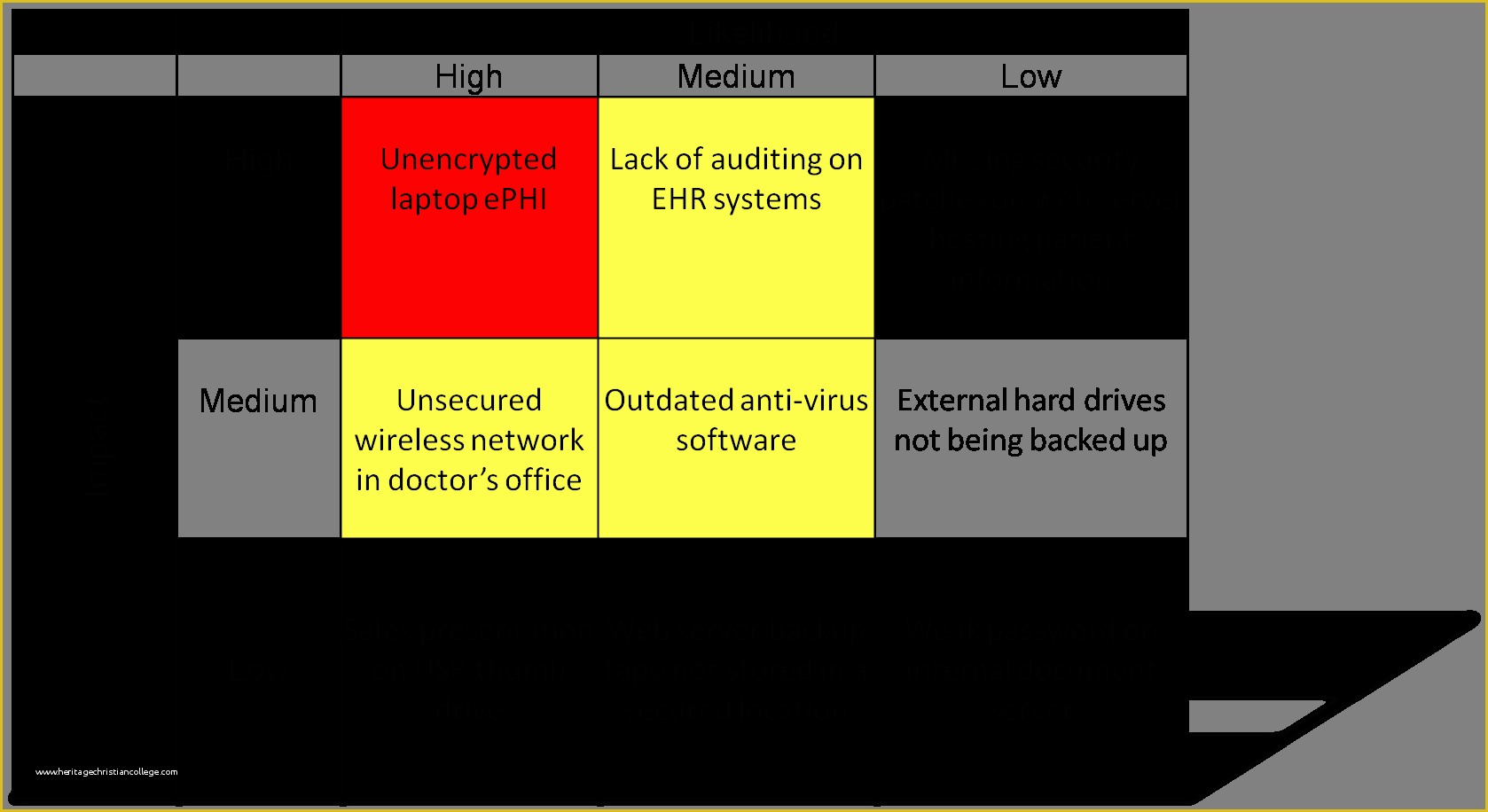
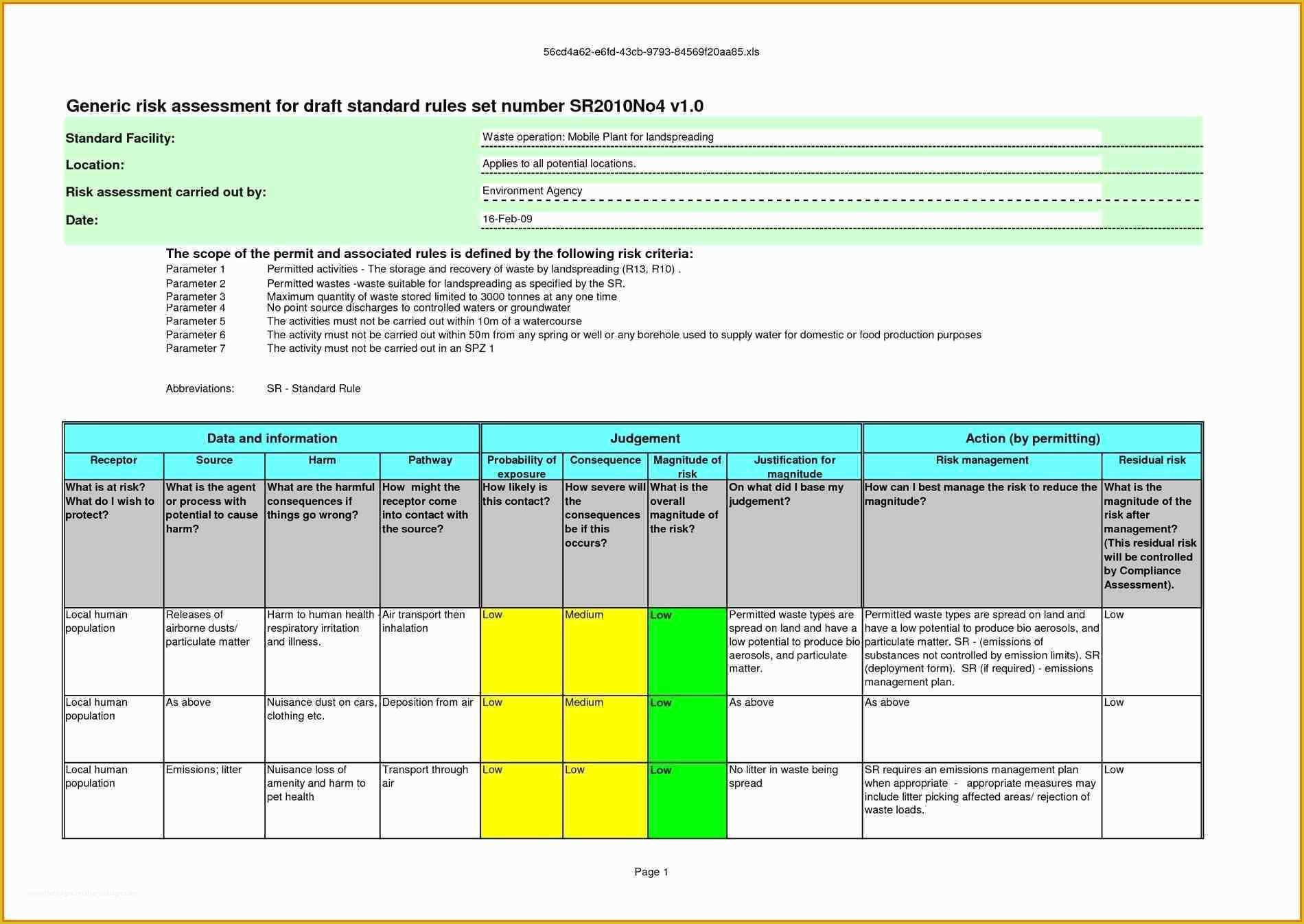
Hipaa Risk Assessment Template Templates Data 5 Hipaa Risk Analysis Template Trtsu Meaningful Use Risk Assessment Template Security Analysis it security risk assessment template – gradyjenkins Consent Form Simple Business Associate Agreement Template Customized HIPAA Training Based on the Job Role of the.
information technology risk assessment checklist hhs releases security risk assessment tool to help providers … hhs releases security risk assessment tool to help providers with hipaa pliance … privacy & security your review or other use of the documents or other information or services on the hipaa cow web site collectively the “documents” will be governed by the terms and conditions stated below hipaa security rule – hipaa academy hipaa security rule standards the hipaa security rule identifies standards and implementation specifications that organizations must meet in order to be e pliant it risk management it risk management is the application of risk management methods to information technology in order to manage it risk i e the business risk associated with the use ownership operation involvement influence and adoption of it within an enterprise or organization datica hipaa pliance policies our pany is built with information security and pliance at its core our policies procedures and technology go above and beyond hipaa pliance to ensure our users data and their users data is secure we take hipaa pliance seriously because we believe it is the right thing to do it security resources for privileged account management it security resources privileged account management solutions on demand webinars videos case stu s and more by thycotic and other industry experts template security and privacy standards cspo tools template information protection standards version 1 05 published by cspo tools inc page 4 name though – just use it inside your organization it grc training governance risk driving grc with information security & information technology the instructors for the grc group’s is it grc certification training program understand that when used properly information technology can drive an organization’s governance risk management and pliance efforts making them both cost effective and sustainable 13 fantastic resources for writing an information security key elements of an information security policy the infosec institute articles these are some of our favorite articles from blogs magazines and other website scattered across the web pliance line packaged training pliance line offers regulatory pliance trainings content grc advisory & consulting on audit risk management corporate governance & plying with laws and regulations
hipaa security ,